What is Zoom Bombing and How to Prevent Zoom Hacking of your Organization?

UPDATED September 28, 2020
Written By Merlene Leano
The onset of the Covid-19 pandemic led many people to work from home and conduct meetings online. One of the dangers of using online platforms for meetings is Zoom bombing. With today's tech-savvy society, the term zoombombing stays a buzzword to the majority. After reading this article, you will be acquainted with what zoombombing really means, its targets, and effective ways to protect your brand from hackers.
Zoom bombing is a rowdy intrusion of an uninvited individual to an online meeting. It's annoying and detrimental to your organization. Therefore, it's important for you to know how you can prevent Zoom bombings in your organization. Read further below to find out what steps you can take to stop it.
What is Zoom Bombing?

Zoom bombing is an occurrence wherein an uninvited stranger suddenly joins a video conference to cause disorder among the participants. It was a breach of security and privacy that involved the popular video conference platform called Zoom. Zoom has been on the rise since the start of the pandemic, with several people and companies resorting to use the software for online classes, meetings, and other important discussions.
An example of Zoom bombing is an online class of students being intruded by a random individual while simultaneously sharing pornographic content.
Often, the uninvited stranger would show off a cheap laugh, talk profanity, speak words that are racially or religiously insulting, share pornographic material, and other inappropriate images that would disrupt and harm the participants of an online video conference.
How do Zoom bombing sessions happen?
Basically, because most Zoom meetings have public links, it makes it effortless for anyone to access a specific Zoom meeting as long as they have a copy of the link. These malicious individuals who merely want to cause disruption would gather Zoom meeting links and forward them to private chat groups where they can all plan out their malicious intrusions.
The careless distribution of Zoom links would often result in strangers or uninvited individuals entering an online video conference without prior notice.
What kind of organizations are affected by zoom bombing?
Zoom bombing has caused serious issues for several sectors and organizations, such as schools, companies, and governmental institutions, worldwide. Such incidents have resulted in increased scrutiny on Zoom as well as restrictions on usage of the platform by world-renowned companies like SpaceX and Google. In response, Zoom, citing the sudden influx of new users due to the COVID-19 pandemic, has been taking measures to increase the security of their teleconferencing application. Incidences of Zoom bombing have prompted the police in various countries to investigate such cases and file criminal charges with those responsible.
How to Protect Your Organization from Zoom Hacking
Good thing, there are safety measures you can follow in order to prevent Zoom hacking and protect your organization’s reputation from strangers and trolls wanting to derange your online video conference.
Enabling/Disabling Features
Pay attention to the following list of features you need to disable and which ones you need to enable to protect your meeting from unwanted intruders.
Enable the following:
- — You need to enable this so you have immediate access to the options during meetings.
- — Enabling this will allow you to monitor who belongs to your group and who attends as a video conference guest.
- — Even before a Zoom bomber gets the chance to speak when your video conference is already "bombed", you can quickly mute the unwanted or uninvited person to keep them from throwing or verbalizing offensive statements and remarks.
- — The waiting room is sometimes called the Zoom purgatory where participants wait to be approved by the host to join the meeting. This is a great option to block Zoom bombers even before they have the chance to disrupt because every participant gets to be approved first before entering the meeting.
- — This option is already set up as default by Zoom to ensure that even if a troll or stranger has your link, he/she cannot join the meeting without the meeting password.
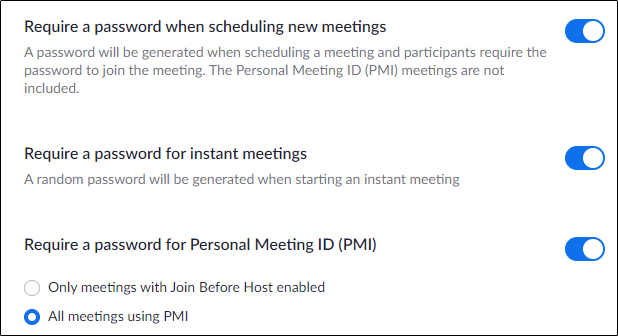
Disable the following:
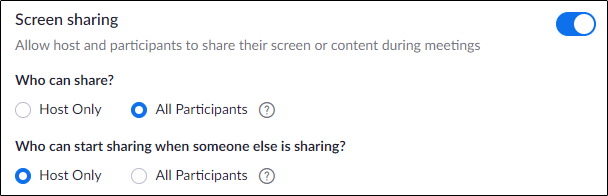
- — To prevent uninvited viewers to share inappropriate content, disable this button. You can either disable it completely or allow only the host to share his/her screen.
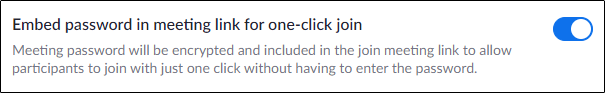
- — Disable this button to prevent any intruder from joining your video conference without any password. Apparently, this option encrypts the password to the "join meeting" link, which defeats the security of your conference.
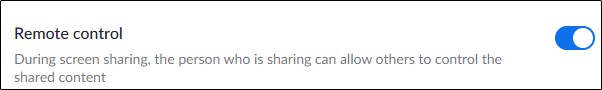
- — As long as you don't need it, it is best to disable this option that allows another participant to take control of another participant's computer system.
- — To prevent files from getting into the hands of unwarranted individuals, disable this button. However, you can also choose certain types of files that you can allow to be shared among the participants.
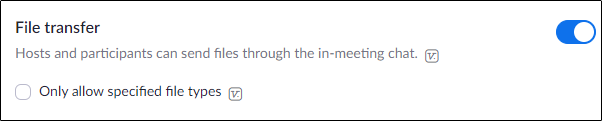
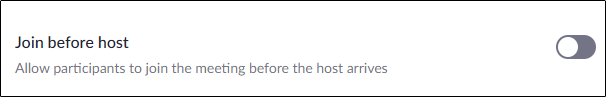
- — The good thing about this feature is it is disabled by default. For security reasons, you should not enable the Join Before Host option. Otherwise, it will allow participants to join a meeting even before the host arrives, and it could risk security and privacy.
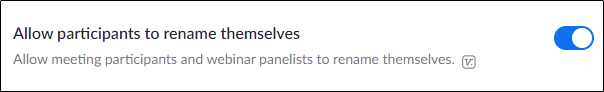
- — Some Zoom hackers or bombers would get their message across by renaming their username, so disable this option.
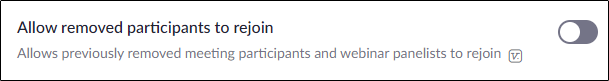
- — This is another button that's been disabled by default to ensure that whenever a Zoom hacker or bomber is kicked out, they can no longer rejoin.
While all these tips are helpful, it should be noted that it is difficult to apply all these for larger businesses and organizations with more participants joining their virtual group discussions. How is safety against internet trolls and hackers of online conferences ensured for large scale businesses?
Incorporate a Live Forum Moderation Through a Third-Party Service

It is fairly more challenging for larger businesses and organizations to manage meetings with a broader coverage without the help of a third-party service. A lot can be missed out without a dedicated group that can look into every aspect of the meeting. This is why it is highly recommended seeking the help of third-party services like Chekkee since they have unique platforms that allow them to help larger businesses in terms of forum moderation.
Some of the Chekkee services you will find useful to stop Zoom bombing are the following:
- 24/7 monitoring of the activities of members
- Eliminating malicious and offensive content
- Implementing forum guidelines
- Keeping threads updated and organized
- Promoting consistency and content relevance
- Upholding member safety and privacy
Conclusion
With the risk brought by Zoom bombing, it's crucial that you think ahead for your business/organization. Incorporate the steps we have mentioned, especially if you have a bigger organization that requires a reliable and efficient service. Our live moderation services assure you that every single aspect of your business and your online meetings are safe all the time. You can check the content and forum moderation services offered by Chekkee to see how we can tailor a lineup of content regulating features according to your business needs. More importantly, our services are powered both by artificial intelligence systems and human-powered services, thus ensuring a full scale protection against hackers and scammers.